Why I call it (anti)-social media, part 2
How social media became a tool to control and monitor you
“The conscious and intelligent manipulation of the organized habits and opinions of the masses is an important element in democratic society. Those who manipulate this unseen mechanism of society constitute an invisible government which is the true ruling power of our country. “
—Edward Bernays, father of modern advertising, public relations, and propaganda, in a book published in 1928.
In part 1 of this series, I introduced you to the technical underpinnings of modern social media, and very briefly explained the nature of the “social graph”. I included some of the material from an older WordPress article that I had written than you can find here.
I concluded part one with this sentence:
“Stay tuned. I’m about to rip away the curtain, show you the machinery behind it, and wake you up.”
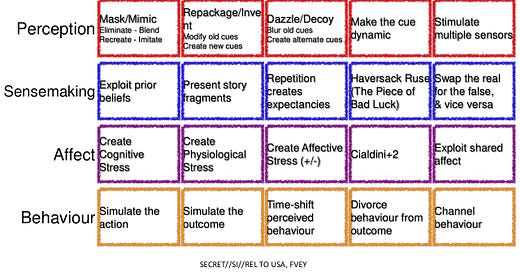
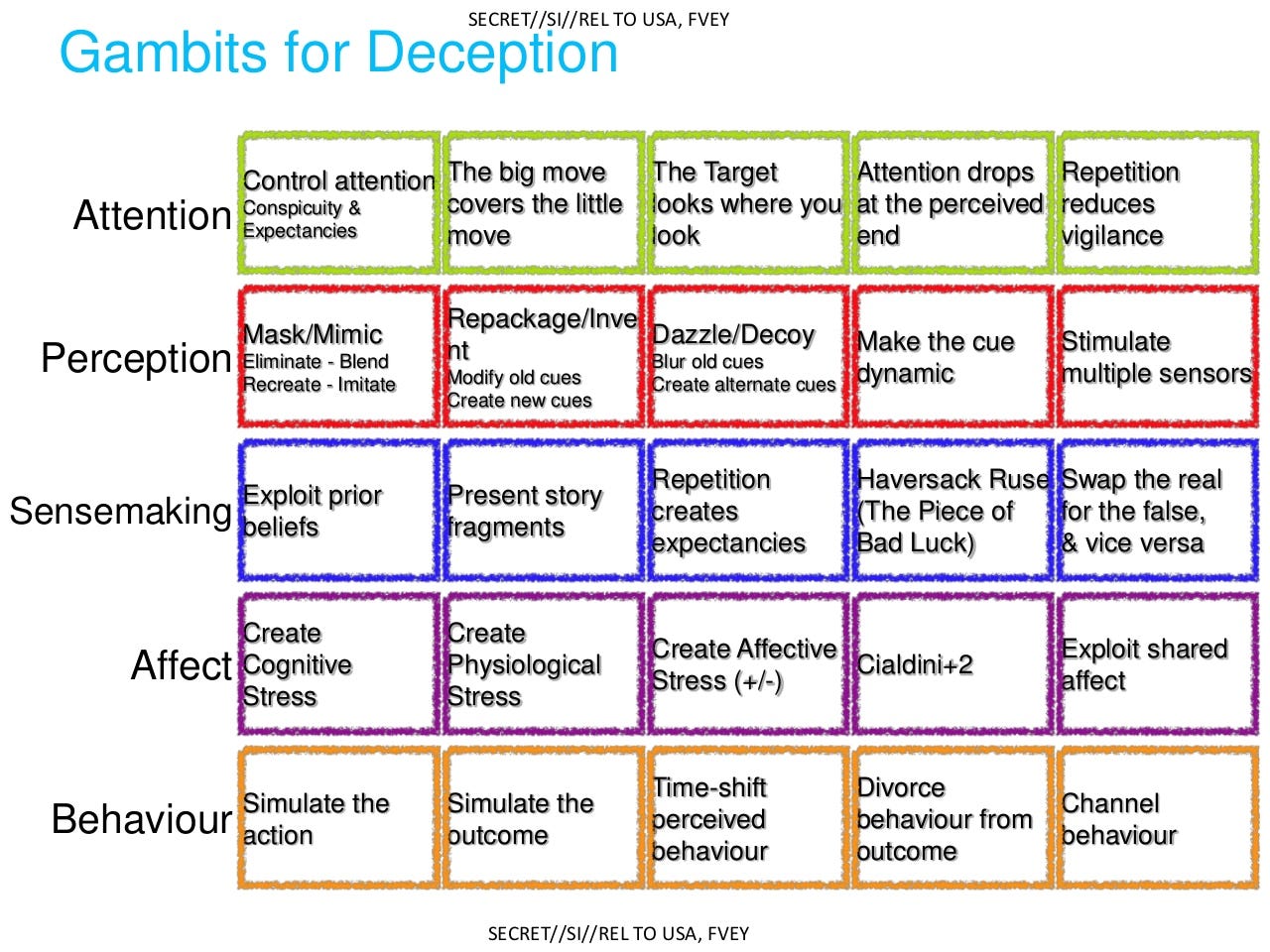
At the end of the first part, I also embedded this image as a lead in to part 2 (this post.) What I want to do here is to tell you where this image came from, and why it begins to lay bare the tools of manipulation that are used against you every day on modern “news” and (anti)-social media.
This image was revealed in a 2014 article by Glenn Greenwald published at theIntercept.com : How Covert Agents Infiltrate the Internet to Manipulate, Deceive, and Destroy Reputations (theintercept.com)
It came from a trove of documents revealed to the world by the Edward Snowden archive. This image is believed to be a slide in a training presentation purportedly from the British GCHQ (an intelligence agency of the UK government analogous to the United States National Security Agency, aka the NSA.)
According to the Intercept article, these GCHQ documents were shared with other countries who were part of the “Five Eyes” alliance: The US, Canada, the UK, Australia, and New Zealand (“FVEY”). This Alliance allows these countries to share certain kinds of signals intelligence among themselves for “security” purposes; but it has been claimed that this arrangement has also been abused. Keep this collection of five countries in mind, because in later posts we’ll talk about some alarming patterns that have appeared in the last few years following the COVID event that apply specifically to these five countries. Often, where there is smoke…there is fire. But that is a topic for a later post.
So—how can the FVEY intelligence sharing system be abused? Here’s an example. US law prohibits the collecting (or after 9/11 and the 2001 Patriot Act, at least revealing) of signals intelligence on US citizens without court-issued warrants1, but it could very well be that a partner agency— in say, Australia— has collected similar signals intelligence on American citizens that the NSA has—but in Australia, access to it isn’t prohibited, because the intercepts are not about Australian citizens. Clever, no?
A US politician with a security clearance might take a visit to Australia, for instance, and be given a secret briefing on what her political opponents in the USA have been emailing or calling each other about. Something that, say, a Secretary of State might be able to do, while she was purportedly visiting Australia for “legitimate State Department” business. It facilitates a “we’ll spy on your people if you’ll spy on ours, and we’ll trade” sort of arrangement, if the allegations are true.
In any case, this slide above reveals that the GCHQ was training its people—and sharing its training materials with others in the FVEY network—on techniques and methods for strategic deception in online forums. Look carefully at the slide above, study it and memorize it, and think about how it might manifest itself in modern social media “conversations”.
Now, you can try to argue that the GCHQ was simply telling intelligence staffers what to look for to detect foreign interference; but it is not a reach to say that they were also telling intelligence staffers how to do this sort of thing themselves. In that Intercept article, you’ll also find this link: Art of Deception
It should no longer be a surprise to you to learn that social media has mutated into a tool far beyond simply selling you on a brand of clothes or shoes. It is now used to not only spy on people, but also conduct psychological warfare operations on populations around the world, subconsciously altering people’s perceptions, attitudes, and political ideas through subliminal and covert means. In fact, if Edward Bernays were alive today, he would be blown away at just how effective a tool to influence and control the masses social media has turned out to be.
Which takes us to the last point of this post. Fear is a powerful tool to mold the perceptions, habits and opinions of people; this has been exploited for centuries. It should come as no surprise that China has a vast army of people - in the millions - who are dedicated to surveilling, spying, and controlling their own population via social media; and that they have also deployed their tools and vast teams of information warriors to influence other countries.
In fact, there is evidence that in the spring of 2020, while the pandemic was picking up steam (which we now have good reason to believe was artificially created in a lab in Wuhan China) there were legions of Chinese PSYOP operators — information warfare soldiers, more properly named — who were deliberately stoking up panic and fear in Italy and other European countries as well as the US. The “lockdown panic” that spread around the world started in Italy, and it was triggered by propagandists from China. There really is an invisible war going on, an Information War, and the casualties are people’s minds.
Many who study this geopolitical era have argued that not only did China plan and execute a strategic release of a biowarfare agent — the virus that causes COVID-19 — to disrupt the world’s economies; but they paired it with a well-planned, well-funded and strategic information warfare campaign.
Anyone who paid attention to the early Twitter and TikTok videos coming out of China showing people falling dead in the streets from “COVID” and armies of people in hazmat suits spraying down buildings and streets should be aware that it was PROPAGANDA. Designed to provoke FEAR. So, too, was the construction of a 20,000-bed field hospital in Wuhan: it was constructed from scratch (using components that were, curiously, already prepared long in advance) in a matter of weeks, and it was just as quickly decommissioned to great public fanfare as a “CCP party success story” a few months later. I watched some of the triumphant Communist Party propaganda videos about this at the time. This, too, was propaganda — and all of this spread around the world because of social media information warfare operations.
How does the CCP use its information army? It sends people into Twitter, Facebook, Telegram, etc. where they use anonymous accounts to spread misinformation, fear, and exploit people’s political or sociological biases to ‘start fights’ in threads by using intentionally inflammatory and incendiary language, among other things.
The goal of China’s Information Warfare units is to weaken its opponents from within: to attempt to provoke civil war, race war, ideological war so that its enemies devour themselves or their economies weaken and collapse during the periods of fear and induced struggle.
Now that you are aware of this, and are somewhat aware of the tactics revealed by that GHCQ document, you should begin to carefully watch and study what you see happening on social media. There are bad actors on all platforms from many different countries, from many “foundations” and NGOs, political parties, and even some for-profit companies that are using your addiction to Facebook, Twitter, Instagram etc. to their strategic advantage. Not only are they spying on you, they are manipulating and influencing your perceptions and beliefs without you knowing it.
As you begin to look at posts and threaded comments with a new jaundiced eye, ask yourself: are these threads of comments truly organic? Who planted these particular ideas in ‘cyberspace’ for us to argue over, at this particular moment, and why? Who exactly ARE these people you have been arguing with online?
How do you know if they are who they claim to be? Why do the “trolls” seem to come in packs, and why do they often all use the same talking points and even copy/pasted language to attack you? Who really is behind those official looking news articles that someone is posting and promoting on social media? Most people won’t read past the headlines, but they are unaware that simply seeing a headline, even if you don’t consciously read it, is often enough to subtly influence you. Bernays was acutely aware of this.
These are all technique of propaganda and psychological warfare, designed to confuse, distract, disorient, disillusion and intimidate you. But once you begin to learn how to spot it, it no longer works.
In part 3, we’ll dive into some examples in more detail, and I’ll share some of my personal experiences detecting and dealing with China’s bot army.
some other time, we’ll talk about the FISC court and FISA warrants, and how this system, intended to protect US Citizens by safeguarding their 4th and 5th amendment rights has also been compromised and abused.


I’m interested in Part 3 and curious why you didn’t post it. Thanks for your work.
I was aware that the Fveys were involved with spying on Trump but was unaware of the Australia concept you put forward. That is bizarre behavior for one of our supposed allies. I guess that means the cabal is active there too. This past year has been a massive awakening - finding that many aspects of public knowledge I've thought was true over the course of my life is NOT. So many things that i can't count them all from the JFK assassination to UFOs being built by multiple corporations to the cabal and deep state among numerous other jolts to my global awareness. Thanks for your time, research and sharing.